Secure Data Destruction for Unix
What is secure computer data destruction? Simply put, securely-deleted data cannot be recovered by any known technique. But when it comes to data security, things are rarely simple. New data recovery methods are developed every year and existing techniques are improved. Security is a relative concept. You can visit this site to get more details on how to secure and manage your data. Much depends on the type of data itself and the way to use it, contact data engineering consultants for a proper management.
Three methods exist for securely destroying data: overwriting, encryption and physical destruction of storage medium. The first two are only applicable to rewritable media. Because degaussing – a common method of disposing of magnetically-recorded data – alters the physical state of storage medium, it falls into the category of physical destruction of data.
Computer data is most commonly stored using three technologies: semiconductor memory (most of which is just tvs diodes in parallel), optical storage, and magnetic storage. In the next decade we will see a shift toward three-dimensional optical storage technologies. Currently, the bulk of computer data worldwide is stored on magnetic medium – hard drives and tapes.
When considering methods for secure destruction of data, we need to evaluate five key characteristics:
- Cost of data recovery. You need to know how expensive will it be for someone to recover a useful amount of data from the storage medium you “erased”.
-
Cost of data deletion. This is how much it will cost you to securely delete your data. Think about how much expertise, time and equipment is required to implement a particular method.
-
Process scalability and sustainability. You may have the resources to securely destroy fifty hard drives this week. What about a hundred hard drives next week? A highly secure but complicated process for data destruction will be pointless if it cannot be followed on a regular basis.
-
Speed of data deletion. In certain circumstance it may be preferable to destroy 90% of data in a few minutes, than 100% in a few days. Certain methods for destroying magnetically-stored data – overwriting and encryption – can be very secure but equally time-consuming.
-
Environmental impact. How much electricity does the data deletion process use? Can the storage media be reused or recycled? Are any pollutants released as byproducts of the process?
These are all corporate organizational issues that must be taken into consideration when developing data management policies. For the purposes of this article, we will leave leave the important tasks of working out policies and procedures to people obviously better equipped to handle this sort of work – managers. Instead, we will concentrate on the unimportant technical aspects of data management.
Let’s start simple: you have a single hard drive with data that needs to be destroyed beyond any reasonable chance of recovery. One approach would involve a sledge hammer, a hard surface and a pair of safety goggles. While destroying data by bashing hard drives with a giant hammer is an excellent way of releasing stress and does not take many years of IT experience, you do need to be in good physical shape. This http://www.sportsandsafetysurfaces.co.uk/surface-types/3g/ may be a problem for many system administrators. Hard drives are small and made of cast aluminum capable of withstanding pressure of many hundreds of pounds per square inch. A sledge hammer will probably crack the hard drive, but there is a good chance that some of the data you are trying to destroy will end up being embedded in some soft part of your body. This would be a complete waste of a perfectly useful system administrator. To make things worse, even a piece of a hard drive’s magnetic platter can be used for partial data recovery. Bashing, bending and shredding hard drives, therefore, would only work if you security requirements are fairly unsophisticated.
Magnetic storage media degaussing is a commonplace process used by most datacenters to dispose of old magnetic tapes and hard drives. While relatively straight-forward, this process is not without its drawbacks. Technically speaking, a degausser does not erase data on a hard drive; it simply reduces the strength of the magnetic field to below the sensitivity threshold of the drive’s read-and-write heads. However, in many cases you can remove the magnetic platters from a degaussed hard drive and use more sensitive specialized equipment to read the data. A degausser’s strength is commonly measured in Oersted (Oe). A degausser with magnetic field strength of around 10,000 Oe (or about 0.8 MA/m) is needed to properly mess up a modern hard drive. Such machines are fairly expensive ($20K+), bulky, and not particularly fast. Often multiple passes through a degausser are required. And still, there is a possibility of data recovery. Everything depends on the sensitivity of the equipment used to read the magnetic platters. Thus some high-security enterprises usually follow degaussing with some form of heat treatment, such as damaging the magnetic platters with a blowtorch or sending the drives to an external vendor to be melted down.
Another disadvantage of the degaussing process is that it renders a hard drive unusable. In many cases you just want to destroy the data and not the disk itself. Unlike hard drives, most tapes can be reused after degaussing. Tapes are also much easier to destroy. There are commercial tape shredders that cost only a couple thousand dollars and will turn your DLT tapes into dust. They also have shredders for hard drives, but those are pricey ($30K+). HDD shredders reduce a hard drive not to dust but to a bunch of shards about half-a-square-inch in size and their effectiveness in destroying data has yet to be certified by any relevant regulatory body. Tapes can also be burned as an effective albeit environmentally irresponsible way of disposing of your storage media (as long as your employees don’t mind the toxic bong fire in the company parking lot). Melting hard drives on site is usually out of the question. Unless of course you are in charge of a datacenter at a steel mill.
GNU shred
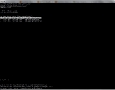
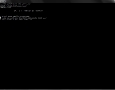
Now that we know that disposing of hard drives securely and efficiently is not as simple as it may sound, let’s take a look at a few simple ways of securely deleting data on a disk, while it is still inside a computer. The first application on our list is GNU “shred”. You will find it pre-installed on many current flavors of Unix (may be called gshred) and Linux (shred). Shred is used to overwrite individual files multiple times with random data before optionally deleting it. Here’s the basic syntax we would use to “shred” /etc/shadow_old:
/usr/bin/shred --force --iterations=30 --remove --verbose --zero /etc/shadow_old
Options used:
--force - change permissions to allow writing
--iterations - the number of times to overwrite the file
--remove - delete the file after overwriting
--verbose - show progress
--zero - perform final overwrite using zeros to hide the shredding process
Sample output:
icebox:/etc # /usr/bin/shred --force --iterations=30 --remove --verbose --zero /etc/shadow_old
/usr/bin/shred: /etc/shadow_old: pass 1/31 (random)...
/usr/bin/shred: /etc/shadow_old: pass 2/31 (911111)...
/usr/bin/shred: /etc/shadow_old: pass 3/31 (555555)...
/usr/bin/shred: /etc/shadow_old: pass 4/31 (edb6db)...
...
/usr/bin/shred: /etc/shadow_old: pass 31/31 (000000)...
/usr/bin/shred: /etc/shadow_old: removing
/usr/bin/shred: /etc/shadow_old: renamed to /etc/0000000000
/usr/bin/shred: /etc/0000000000: renamed to /etc/000000000
/usr/bin/shred: /etc/000000000: renamed to /etc/00000000
/usr/bin/shred: /etc/00000000: renamed to /etc/0000000
/usr/bin/shred: /etc/0000000: renamed to /etc/000000
/usr/bin/shred: /etc/000000: renamed to /etc/00000
/usr/bin/shred: /etc/00000: renamed to /etc/0000
/usr/bin/shred: /etc/0000: renamed to /etc/000
/usr/bin/shred: /etc/000: renamed to /etc/00
/usr/bin/shred: /etc/00: renamed to /etc/0
/usr/bin/shred: /etc/shadow_old: removed
Because “shred” does not support recursive operations, to delete multiple files you will need to use “shred” in conjunction with a simple loop reading a file list or with the “find” command. In the following example we will find and shred all shadow* files in /tmp.
find /tmp -type f -name "shadow*" -exec /usr/bin/shred --force --iterations=30 --remove --verbose --zero {} ;
TestDisk and PhotoRec
Before we can continue discussing various file-deleting and disk-wiping applications, we need to find some way of gauging their effectiveness. TestDisk and PhotoRec are two relatively easy-to-use file and disk recovery open-source applications released under GNU GPL. You can find precompiled versions of these apps for most Solaris and most Linux flavors. For our next example, we will create a directory containing a text file with a unique string that can be easily identified. We will then delete this file using the “rm” command and try to recover it with TestDisk/PhotoRec. We will then repeat the process, but this time we will use “shred” instead of “rm” to remove the file.
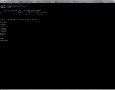
Prepare file for the test:
icebox:/etc # mkdir /tmp/testdisk
echo "p17n87uu2377b66" > /tmp/testdisk/secret_file.txt
Remove files:
icebox:/etc # rm /tmp/testdisk/secret_file.txt
icebox:/etc # ls /tmp/testdisk/
icebox:/etc #
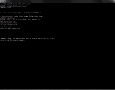
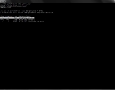
Take a look at the partitioning tables for the available hard drives. The /tmp/testdisk is mounted on /dev/sda2:
icebox:/tmp/testdisk # fdisk -l
Disk /dev/sda: 320.0 GB, 320072933376 bytes
255 heads, 63 sectors/track, 38913 cylinders
Units = cylinders of 16065 * 512 = 8225280 bytes
Disk identifier: 0x000a2bbd
Device Boot Start End Blocks Id System
/dev/sda1 1 523 4200966 82 Linux swap / Solaris
/dev/sda2 * 524 9989 76035645 83 Linux
/dev/sda3 9990 19457 76051710 83 Linux
Disk /dev/sdb: 1000.2 GB, 1000204886016 bytes
255 heads, 63 sectors/track, 121601 cylinders
Units = cylinders of 16065 * 512 = 8225280 bytes
Disk identifier: 0x000cd5e7
Device Boot Start End Blocks Id System
/dev/sdb1 1 121601 976760001 83 Linux
Disk /dev/sdc: 1000.2 GB, 1000204886016 bytes
255 heads, 63 sectors/track, 121601 cylinders
Units = cylinders of 16065 * 512 = 8225280 bytes
Disk identifier: 0x00074e90
Device Boot Start End Blocks Id System
/dev/sdc1 1 121536 976229887 83 Linux
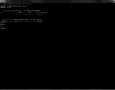
Use PhotoRec to recover all deleted files on a partition:
icebox:/disk1/photorec # photorec
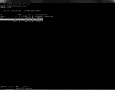
Once PhotoRec is done analyzing the partition – a process that may take from a few minutes to a few hours – all recovered files will be stored in a directory of your choosing. In our case it is /disk1/photorec. Now we need to analyze all text files in this directory to see if PhotoRec managed to recover our secret file. Because we can only recover contents of a deleted file and not its original name, we will have to scan every *.txt file found by PhotoRec for the unique string originally contained in the /tmp/testdisk/secret_file.txt file.
icebox:/disk1/photorec # ls
photorec.ses recup_dir.1 recup_dir.2 recup_dir.3 recup_dir.4 recup_dir.5
icebox:/disk1/photorec # find . -type f -name "*.txt" | while read line
> do
> if [ `grep -c "p17n87uu2377b66" "$line"` -gt 0 ]
> then
> echo $line
> fi
> done
./recup_dir.1/f0040314.txt
icebox:/disk1/photorec # cat ./recup_dir.1/f0040314.txt
p17n87uu2377b66
And so in a few minutes we managed to recover the /tmp/testdisk/secret_file.txt file deleted using the standard “rm” command. Now we repeat the same process, only this time we will use the “shred” command to remove the file.


![Plundering Facebook Photo Albums wyryr1sn52gntzn65v4fpz5lc6v[1]](https://i2.wp.com/www.krazyworks.com/wp-content/uploads/2021/08/wyryr1sn52gntzn65v4fpz5lc6v1-80x80.jpg)
![Scraping a Web Page in Bash clfud46mxf2t5zph2l04zlpgl1d[1]](https://i2.wp.com/www.krazyworks.com/wp-content/uploads/2021/08/clfud46mxf2t5zph2l04zlpgl1d1-80x80.jpg)
![Processing Videos with ffmpeg and Lightroom DSCF5361[1]](https://i1.wp.com/www.krazyworks.com/wp-content/uploads/2020/10/DSCF53611-80x80.jpg)
![Searching Twitter Cat-Devouring-A-Bird-Pablo-Picasso[1]](https://i0.wp.com/www.krazyworks.com/wp-content/uploads/2020/10/Cat-Devouring-A-Bird-Pablo-Picasso1-80x80.jpg)
![Generating Random Text Files for Testing 91ebozy1e3b138waujy28agrngy[1]](https://i2.wp.com/www.krazyworks.com/wp-content/uploads/2021/08/91ebozy1e3b138waujy28agrngy1-80x80.jpg)
![Finding Cron Jobs iwoau71okwxqh4jv3k4ook32qps[1]](https://i2.wp.com/www.krazyworks.com/wp-content/uploads/2021/08/iwoau71okwxqh4jv3k4ook32qps1-80x80.jpg)
![Understanding Memory Utilization in Linux 5gtysva4wkc8mzc1k3e66vaycxx[1]](https://i1.wp.com/www.krazyworks.com/wp-content/uploads/2021/08/5gtysva4wkc8mzc1k3e66vaycxx1-80x80.jpg)
![Validating HTTPS Cache Peers for Squid sy2zeb1vp2h8itlxfbbylw0jrm0[1]](https://i0.wp.com/www.krazyworks.com/wp-content/uploads/2019/12/sy2zeb1vp2h8itlxfbbylw0jrm01-80x80.jpg)
![Verifying SNMP Connectivity on Multiple Hosts Photo-2019-10-07-14-39-03_0266[1]](https://i1.wp.com/www.krazyworks.com/wp-content/uploads/2019/11/Photo-2019-10-07-14-39-03_02661-80x80.jpg)
